Don’t just learn about CSV… learn to do CSV
Would you expect to get fit by watching a personal trainer work out?
Would you expect to learn to drive by watching an instructor behind the wheel?
Would you expect to speak a new language just by listening to others?
Of course not.
And you don’t learn Computer System Validation by sitting through a lecture – or guessing the right answer on a quiz.
You learn it by doing it.
Practical Application – Write a 6,000-Word Technical Report
For your End of Module Assignment, you will replicate what your validation manager would ask you to do in a real work setting.
You will write a 6,000-word technical report on a GxP computerized system application of your choice, to present to senior management.
Your report will help management make critical decisions about the electronic data generated and managed by the system, (e.g. will it meet the findings from a previous FDA/EMA audit, or to prepare for an upcoming audit, etc).
You can choose a project based on a system you work with. Your report should:
- Identify and describe typical business and GMP functions
- Schematically represent typical architectural components
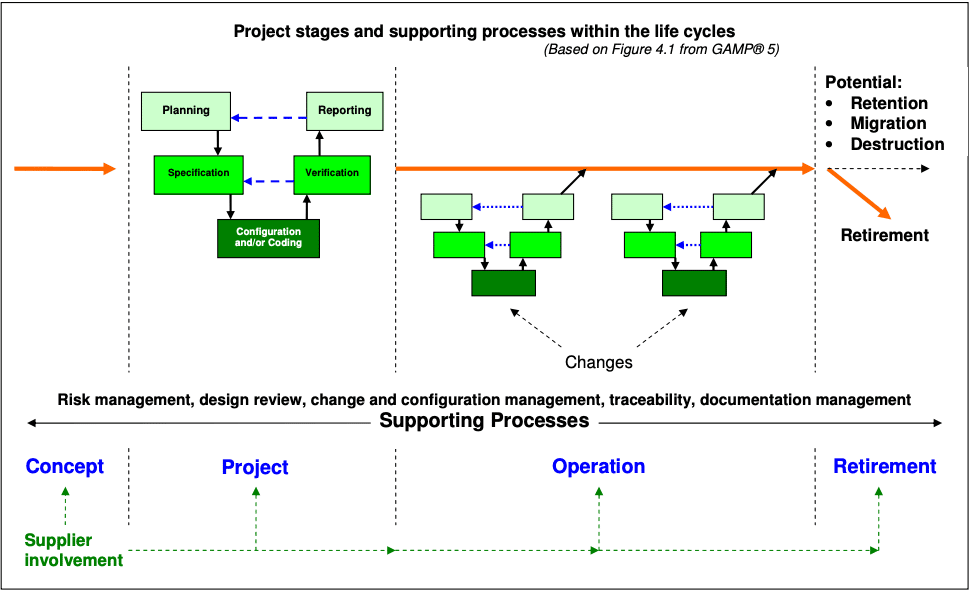
- Describe a general approach to achieving compliance and fitness for intended use over the entire lifecycle from:
- Concept
- Project
- Operation
- Retirement
Prove your Expertise at a Job Interview
Take your completed report on a GxP computerized system to a job interview to demonstrate your expertise.
Who should take a CSV course?
Key aspects covered in this CSV course…
- Regulatory Requirements:
Understand and apply guidelines from the FDA governing the use of electronic records and signatures in a regulated environment such as 21 CFR 211.68, 21 CFR Part 11, and international regulations such as EudraLex Volume 4 — Annex 11, ICH and PICs - GAMP Framework:
Learning the Good Manufacturing Practice (GMP) framework, especially GAMP 5, for computer system validation. - Validation Lifecycle:
The course will guide you through the entire software validation life cycle from design, through construction, installation and live start-up. And it will explain how the CSV process fits into your Software Life Cycle and the purpose of each validation deliverable. - Risk Management:
Learn the methodology and implementation model for a risk-based approach to CSV. - Quality Assurance
The principles of your software quality assurance and how to manage the auditors’ expectations around its key components. - Data Integrity:
Understanding the importance of data integrity in the context of computerized systems and how validation ensures data reliability.
You’ll produce a number of deliverables throughout the course including…
- Determine the end-user supplier activities during the lifecycle of a computerized system
- Identify where you would use risk-based decision-making throughout the lifecycle of a computerized system
- Prepare a configuration management process flow diagram and identify where to use change control
- Define the content of typical logs and accompanying records for both incident management and corrective and preventive action (CAPA)
- Complete 8-question booklets (one for every week’s worth of content) which will summarise what you have learnt for the week and ensure you retain and understand the information.
- Write a 6,000-word technical report to present to senior management on a GxP computerized system application of your choice.
And take the following skills and knowledge back to work…
- Be able to apply the FDA and international regulations to your current projects
- Use Risk-based decision when making an assessment to see what software does or does not require validation, ensure critical risks are identified and the correct level of validation is carried out.
- Create key validation deliverables, including validation plans, requirements specifications, test plans, validation tests (IQ, OQ, PQ), trace matrices, test summaries, and validation reports
Course Price →
Minimum Entry Requirements
This program is highly specialized so you MUST have:
- a solid understanding of Good Manufacturing Practices(GMPs), or Good Laboratory Practices (GLP), or Good Clinical Practices (GLP), or other GxP rules, regulations, and guidelines.
- solid experience using at least one GxP computerized system application and understand its functional layout.
AND you must be one of the following…
- PhD, Masters or Degree in Biochemistry, Microbiology, Molecular Biology, Lab/Science, etc
- Validation Engineer/Specialist or Senior Validation Manager
- Automation, Control/Instrumentation, Process, Chemical, etc Engineer or Technician
- Quality Assurance or Quality Control Technician or Specialist
- Maintenance Engineer, Technician or Specialist
- Front/Backend Developer
- Cyber Security
Not sure if you meet the minimum requirements? Contact us!
NOTE: If you don’t have a solid understanding of GMP rules, regulations and guidelines, you need to start with our 6-week GMP Training For Beginners in the Pharmaceutical Industry. (There’s a special price reduction for this GMP program if taken together with our CSV course. Contact us for details)
What is Computer System Validation (CSV)?
Computer system validation is a process used to ensure (and document) that all computer-based systems will produce information or data that is accurate, secure, reliable and traceable. The pharma and med device sectors use computer systems to operate and record a range of regulated processes and activities from clinical trials, manufacturing, product testing, distribution, storage, logistics, etc so it’s critical that these systems can be relied upon to:
- produce data accurately and consistently
- create an indelible electronic data trail that is transparent, traceable and tamper-proof
- store those electronic data records in a way that is safe, secure and can stand the test of time
Your 10 week class schedule:
Delivered by a practicing industry expert
Dr. Joe Brady
Full-Time Validation Lead
Lecturer, Technological University Dublin, Ireland
Senior Associate, GetReskilled
Dr. Joe Brady is a full-time practicing Validation Lead and an assistant lecturer with Technological University Dublin (TU Dublin), in the School of Chemical and Pharmaceutical Sciences. Joe is a certified trainer and highly experienced in competency-based training. He designs and prepares educational modules and full academic courses ranging from MSc, MEngSc. BSc, to Certificate level, for a range of academic institution.
He is also a supervisor for MSc/MEngSc and PhD theses. Joe has over twenty years of project experience in the pharmaceutical, biopharmaceutical and medical device industries in Ireland, Singapore, China, The Netherlands, France and the USA.
Hear from people who’ve taken this course

Shane Flynn

“I found the Computer System Validation Training Course to be very well structured and detailed”
“All sections of the course were explained well and the online delivery allowed for a flexible study plan which was very beneficial when working alongside study. The end of module assignments targeted key points in the lectures which was useful when writing the final assignment. I found this course very useful in my current role and would highly recommend it to anyone looking to gain knowledge in Computer System Validation.”

Ken O’Keeffe
“Interesting and Helpful in my Current Role”
“I have found the Computer System Validation Course to be both interesting and helpful in my current role. The individual sections of the course are easy to follow. The delivery of the course is really straight forward. During the course there has been times when I have been busy with work and have not been able to study. The structure of the course allows me to be flexible in my study.”

Giorgia Romeo
“I Would Highly Recommend This CSV Course”
“I would highly recommend anyone wishing to gain an education in the Computer System Validation sector to do this course. For me it has been very useful studying on-line in order to do the course in my own time. Lessons are very clear and the assignment deadlines make you disciplined to meet the deadlines set.”
How We Deliver Our Online Courses without ZOOM Classes
With every GetReskilled ONLINE program;
- Centralized Platform: We use one platform (Moodle) where you can log into your classroom anytime. Each week, you’ll watch videos and complete quizzes, tests, interactive activities, and projects. The course materials are available 24/7, so you don’t have to be online at a specific time. There are No Zoom Classes. Study anywhere, anytime, such as after the kids are in bed or on the weekend.
- Flexible Schedule: Your working schedule may be unpredictable, so we offer flexible delivery. You can slow down, speed up, or pause the program as needed.
- Progress Checks: We release one week’s worth of material at a time and manually check your activity logs at the end of each week to ensure you are keeping up with your work.
- Dedicated Course Leader: Your course leader will:
- Help you create a weekly study plan
- Answer any questions
- Check your progress every Monday
- Follow up regularly to support you until the end of the course.
This all helps us to spot any potential issues early and helps you completely finish the program.
Contact Details For This Course
Geraldine Creaner
Earn a GxP Computer System Validation Certificate
Add details of your CSV certificate to your CV/Resume or your LinkedIn profile.

Price
$799/month
For 4 months
Or $2,899 in Advance
Enroll a Team of 5 People
$11,596
Save $2,899
10 Day Fast Track Option with Priority Support
$3,999
- Complete this program in 10 days.
- Your course leader will check your progress every morning and follow up with you to keep you on schedule.
- We can start you within 24 working hours upon receipt of payment.
- Contact us for details.
€699/month
For 4 months
Or €2,699 in Advance
Enroll a Team of 5 People
€10,796
Save €2,699
10 Day Fast Track Option with Priority Support
€3,999
- Complete this program in 10 days.
- Your course leader will check your progress every morning and follow up with you to keep you on schedule.
- We can start you within 24 working hours upon receipt of payment.
- Contact us for details.
£649/month
For 4 months
Or £2,299 in Advance
Enroll a Team of 5 People
£9,196
Save £2,299
10 Day Fast Track Option with Priority Support
£3,499
- Complete this program in 10 days.
- Your course leader will check your progress every morning and follow up with you to keep you on schedule.
- We can start you within 24 working hours upon receipt of payment.
- Contact us for details.
Price
€699/month
For 4 months
Or €2,699 in Advance
Enroll a Team of 5 People
€10,796
Save €2,699
10 Day Fast Track Option with Priority Support
€3,999
- Complete this program in 10 days.
- Your course leader will check your progress every morning and follow up with you to keep you on schedule.
- We can start you within 24 working hours upon receipt of payment.
- Contact us for details.
$799/month
For 4 months
Or $2,899 in Advance
Enroll a Team of 5 People
$11,596
Save $2,899
10 Day Fast Track Option with Priority Support
$3,999
- Complete this program in 10 days.
- Your course leader will check your progress every morning and follow up with you to keep you on schedule.
- We can start you within 24 working hours upon receipt of payment.
- Contact us for details.
£649/month
For 4 months
Or £2,299 in Advance
Enroll a Team of 5 People
£9,196
Save £2,299
10 Day Fast Track Option with Priority Support
£3,499
- Complete this program in 10 days.
- Your course leader will check your progress every morning and follow up with you to keep you on schedule.
- We can start you within 24 working hours upon receipt of payment.
- Contact us for details.
Price
£649/month
For 4 months
Or £2,299 in Advance
Enroll a Team of 5 People
£9,196
Save £2,299
10 Day Fast Track Option with Priority Support
£3,499
- Complete this program in 10 days.
- Your course leader will check your progress every morning and follow up with you to keep you on schedule.
- We can start you within 24 working hours upon receipt of payment.
- Contact us for details.
€699/month
For 4 months
Or €2,699 in Advance
Enroll a Team of 5 People
€10,796
Save €2,699
10 Day Fast Track Option with Priority Support
€3,999
- Complete this program in 10 days.
- Your course leader will check your progress every morning and follow up with you to keep you on schedule.
- We can start you within 24 working hours upon receipt of payment.
- Contact us for details.
$799/month
For 4 months
Or $2,899 in Advance
Enroll a Team of 5 People
$11,596
Save $2,899
10 Day Fast Track Option with Priority Support
$3,999
- Complete this program in 10 days.
- Your course leader will check your progress every morning and follow up with you to keep you on schedule.
- We can start you within 24 working hours upon receipt of payment.
- Contact us for details.
Application Deadline: Wednesday 9th July
Program Starts: 16th July
Start your application
Get certified and extend you or your team’s role to CSV Projects
Contact Details For This Course
Geraldine Creaner
Got more questions?

Hi, I’m Donagh Fitzgerald. Chat with me live anytime – just click the blue chat bubble in the bottom-right corner of the page.
I’m online Monday to Friday during working hours (Irish/UK time).
If I’m away from my desk, leave a message and I’ll get back to you as soon as I can.
Or you can fill out the form below and we’ll reply within one working day.


